Share
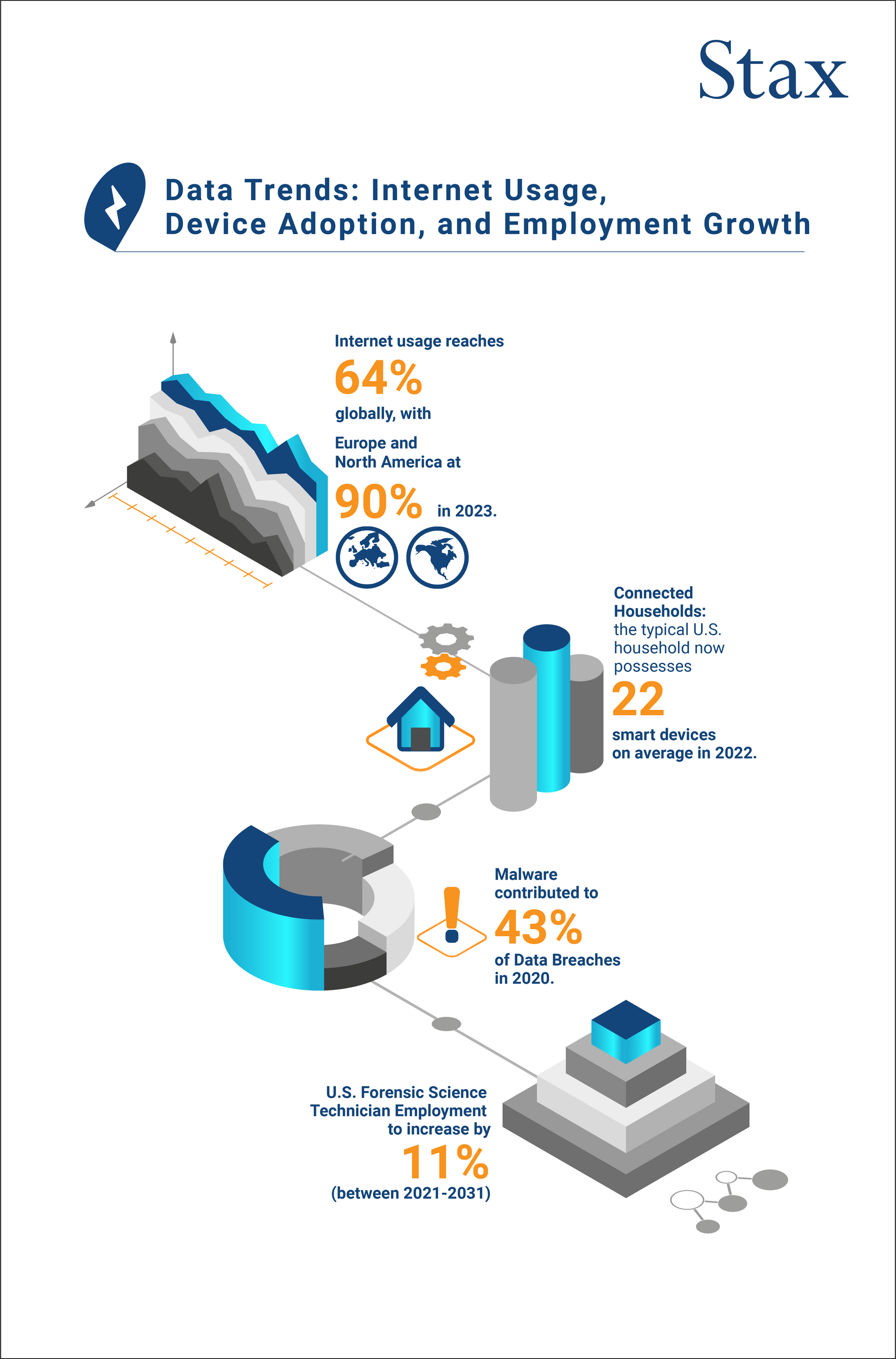
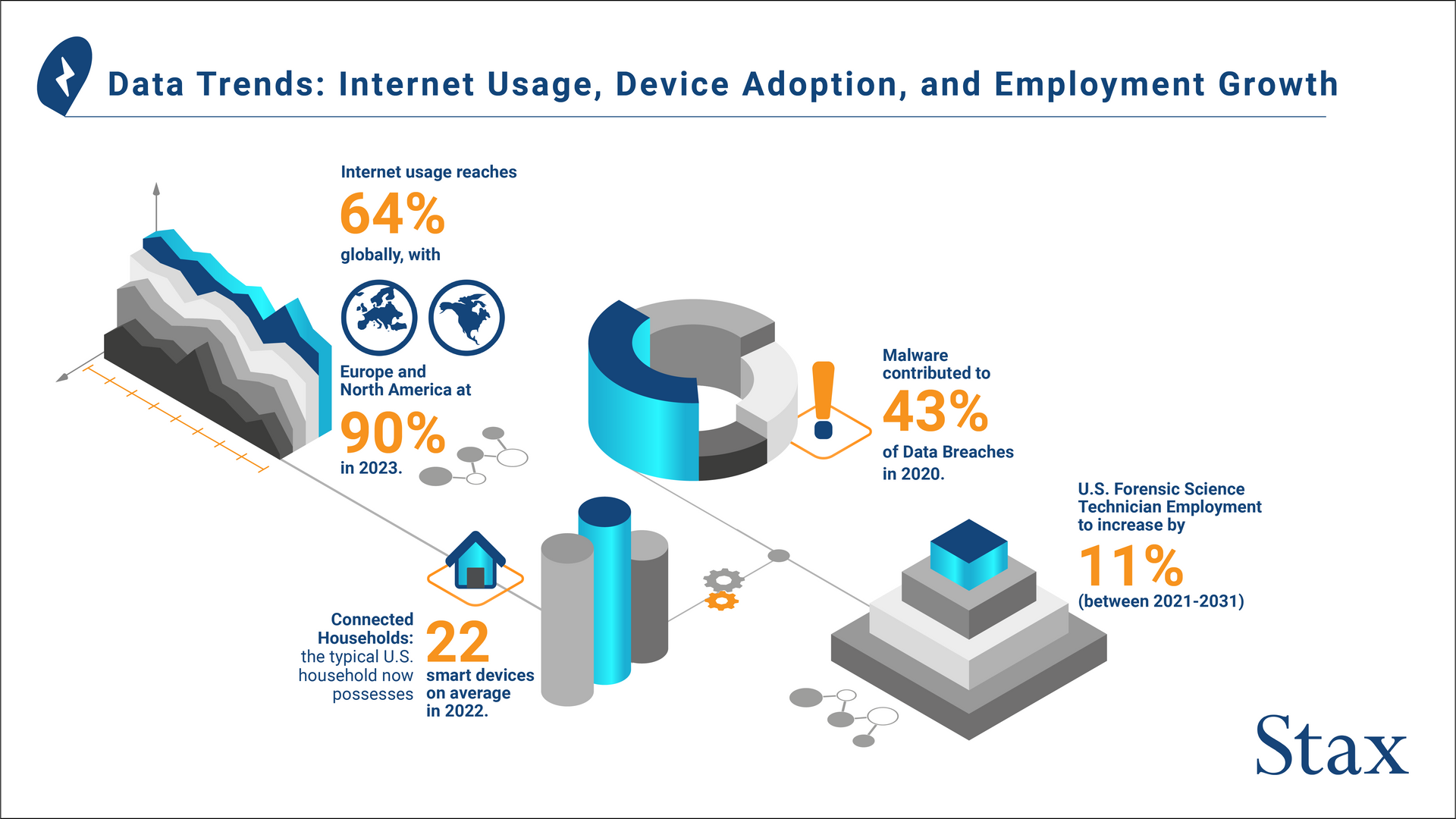
Digital Forensics (DF) is crucial to investigating incidents that involve the use of technology to commit criminal acts. Growth in the utilization of connected devices globally has expanded their use case over the years. According to a report published by Deloitte, the average number of smart devices, such as laptops, smartphones, smart watches etc., was 22 per U.S. household in 2022. At the beginning of 2023, 64% of the world’s population was using the internet¹, this statistic jumps to 90% if we consider only Europe and North America.
Furthermore, during the pandemic, organizations were forced to go through rapid digital transformation to remain viable. With employees and systems moving online, a company’s exposure to cyber risk increased significantly. In a 2023 PwC report, 39% of CEOs have identified cyber risk as the highest exposure their companies will face over the next five years². In a similar global survey conducted by PwC, ransomware, phishing, supply chain attacks, and impersonation were identified as the biggest cyber-risk challenges.
According to the Bureau of Labour Statistics, employment of forensic science technicians is expected to grow by 11% from 2021 to 2031 in the U.S., significantly faster than the average job growth, in order to meet demand.
Types of Cyber Threats
Malware is a type of software that is created to damage and/or steal information from computer systems. It can take many forms, including viruses, worms, trojans, ransomware, and spyware. These can spread through infected email attachments, malicious websites, or by exploiting vulnerabilities in software. Malware has been a growing issue for businesses in the U.S. with 43% of data breaches involving malware in 2020, according to a Verizon data breach investigations report.
Phishing is another preferred mode for hackers. It is a type of cyberattack in which criminals use fake emails, websites, or messages to trick individuals into providing sensitive information such as passwords and credit card details. With the onset of the pandemic, phishing attacks have become more advanced and now often mimic official links from tech platforms such as Skype, Zoom, and Google Meet. In April 2020, Google’s Threat Analysis Group blocked 18 million phishing emails related to the Covid-19 pandemic each day.
Another mode of cyber-attack that is has been growing more rapidly in the U.S. is a Denial-of-Service (DoS) attack. This is a type of cyber-attack that disrupts business operations by flooding a network with false requests. This makes it difficult for users to access resources such as email, websites, and online accounts. DoS attacks typically don't result in lost data, but can still cost time, money, and other resources to resolve.
Digital Forensics Tools and Solutions
The digital information universe is vast. Tools can fall into several categories, including database forensics, mobile device analysis, email analysis, internet analysis, network forensics, social media forensics, etc. As such, companies in the space predominately specialize in point-solutions. Some of the most used tools include:
This is the most well-known digital forensics tool, utillized to examine a range of digital media, including hard drives, CD-ROMs, DVDs, and memory cards. It includes a set of command-line tools that allow a digital forensics examiner to perform tasks such as file system analysis, file recovery, and keyword searching.
For tools such as Sleuth Kit to be effective, original digital copies of hard drives must be preserved before evidence can be extracted. FTK Imager does this seamlessly by analyzing drive images and preserving the integrity of evidence without altering its original state.
This is a non-profit organization dedicated to advancing memory (RAM) analytics in the digital forensics’ community. The software is used for malware detection and incident response, allowing for the preservation of evidence stored in memory that might get lost in the event of a system shutdown.
Several tools developed in the space, including the three listed above, utilize open-source software which makes them freely available and modifiable for different use cases. Furthermore, as findings from DF investigations are often used to present evidence in a court of law, tools are designed to be utilized in a forensically sound manner−which means they do not modify the original data and maintain a clear chain of custody throughout the investigation.
Challenges Faced by the Digital Forensics Industry
Significant growth in connected devices is posing a challenge to the market, with the demand for digital forensics examinations increasing by 11-16% over the last several years, causing backlogs and delays³.
Preservation of user privacy when sifting through data to reconstruct a crime can be a complex task.
The sophisticated and complex nature of emerging technologies such as IoT, cloud computing, and artificial intelligence require continual updates to tools and technologies−while maintaining data integrity⁴. This can be both challenging and time consuming.
Law enforcement agencies rely on third parties to deliver DF expertise. However, shrinking budgets and resources are resulting in severe backlogs and the inability to capture critical information pertinent to an investigation⁶. The utilization of open-source digital forensics tools helps to combat this challenge.
Despite the industry challenges, the demand for DF tools will inevitably continue to grow as cyber risks dominate C-suite agendas, creating new opportunities for investments in the space. Read more in our article about the Rising Digital Evidence and Data Breaches Boost Demand for Digital Forensics.
Sources
- Connectivity and Mobile Trends Survey, Deloitte, 2019
- Digital 2022: Global Overview Report, Simon Kemp, We Are Social, Hootsuite, 2022
- How Many People Use the Internet in 2022? (Global Statistics), Oberlo, 2022
- CEO Survey: Cybersecurity and Privacy, PwC, 2022
- Top 5 cyber threats businesses can’t ignore, PwC Mauritius, 2019
- https://www.bls.gov/ooh/life-physical-and-social-science/forensic-science-technicians.htm
- 2020 Data Breach Investigations Report, Verizon Business, 2020
- Findings: COVID-19 and online security threats, Google, April 15, 2020
- Cost of a Data Breach Report 2022, IBM Security, 2022
- Digital IT Forensics: Evolution Through Digital Transformation, ISACA Now, 2022